Samsung declares new Cosmic system Watch 4, drops iOS support for new wearables
New watch will not help iPhones; key components are restrictive to World telephones.
by Corey Gaskin
The Universe Watch 4
Samsung
Samsung just wrapped its 2021 Unloaded occasion, and as well as delivering a couple of top of the line foldable telephones, the organization declared new System Watches. The watches' plans have been refreshed decently, as have their innards, and they will be the first smartwatches running Google and Samsung's new Wear operating system.
Interestingly—and maybe because of the Google/Samsung coordinated effort—the new Cosmic system Watch 4 and World Watch 4 Exemplary can not match with iOS gadgets. Samsung disclosed to us that it as of now has no designs to stop heritage support for past World Watches that were viable with iOS gadgets.
Google's redone Wear operating system stage was first declared at Google I/O recently as a cooperation among Samsung and Google. The new World Watches give us our first look at the product since the declaration.
Until further notice, it appears to be that marginally more extensive application similarity is the primary component on the product front. Equipment might be the greatest benefit, however, as Samsung's chips, similar to the new Exynos W920 in the Universe Watch 4, will be accessible to all future Google wearables, which frantically need equipment updates.
The Universe Watch 4 uses bioelectrical impedance investigation to quantify body creation in under 15 seconds.
Samsung's skin, One UI Watch, overlays the new Wear operating system on the Watch 4. The style have been upgraded and show up more moderate and basic, yet the essential capacities continue as before. The Watch has a back and home catch, just as a computerized bezel for looking through records and screens all through the UI. The World Watch 4 Exemplary will have a genuinely pivoting bezel for similar capacities. Both watches are 5ATM and iP68 evaluated. Samsung says the watches have as long as 40 hours of battery, probably because of low-power modes that limit usefulness.
Samsung Wellbeing Experience
Home and back buttons are used for both the Watch 4 and Watch 4 Classic. The former has a digital bezel for navigation.
Similar to the case in past Universe watches, two chief wellbeing highlights—ECG and pulse checking—are simply accessible to those utilizing viable Samsung Cosmic system telephones.
Pulse checking is as yet inaccessible in the US, and a few nations will not get ECG readings. The Universe Watch 4 uses another, restrictive sensor for following these wellbeing measurements; it screens optical pulse (circulatory strain, pulse), electrical pulse (ECG), and bioelectrical impedance investigation (BIA).
The Classic opts for a physical rotating bezel. It's also bigger, at 42 or 46 mm.
Body creation estimation and the connected BIA sensor are new increases to the System Watch series. Samsung says the Watch 4 will gauge skeletal bulk, basal metabolic rate, body water, and muscle to fat ratio—all in around 15 seconds. The organization says the estimations come to inside 98% exactness of DEXA bone thickness examines, the current highest quality level. SpO2 observing is likewise ready and will assist with rest following specifically.
Blood oxygen levels are checked once consistently during rest, pair with another sound wheezing discovery highlight for your telephone. The entirety of your wellbeing data is signed in the Samsung Wellbeing Screen application, where you can likewise take part in group based difficulties with loved ones.
The Watch 4 is available in 40 or 44 mm versions in a variety of colors.
The Cosmic system Watch 4 and World Watch 4 Exemplary come in aluminum and treated steel watch cases, individually. The Watch 4 offers 40 mm and 44 mm sizes, while the Exemplary comes in 42 mm and 46 mm sizes.
Watch bands of various colors will also be available.
The two adaptations have Bluetooth and LTE-prepared variants, what start at $250 for the Bluetooth Cosmic system Watch 4 and $350 for the Work of art.
But the classic comes in only black or silver.
Pre-orders are accessible now, with transportation beginning on August 27. The individuals who pre-request between August 11 and August 26 can get a $50 Samsung credit "while supplies lastArs Technica←→
2. macOS Big Sur 11.5.2 is here, but it doesn’t seem to do much
We probably won't see any new macOS features until Monterey later this year.
by Samuel Axon
The front of the 24-inch iMac with Apple's M1 chip.
Samuel Axon
Today, Apple released a new version of its Mac operating system, macOS Big Sur. The new update is labeled macOS Big Sur 11.5.2, but there aren't any new features or major security updates. Rather, macOS 11.5.2 focuses on "bug fixes." In fact, these are Apple's release notes for the latest version of Big Sur, in their entirety:
macOS 11.5.2 includes bug fixes for your Mac.
As you can see, the release notes do not specify which bugs have been fixed and mention no new features. Apple maintains a support page where it details the security updates within a given release, too. But that's bare for this release. "This update has no published CVE entries," it says.
While Apple often (but not always) releases software updates for many or all of its platforms at the same time, macOS was alone today—at least in terms of public releases. Today also saw major new beta releases of iOS 15, watchOS 8, macOS Monterey, and more.
macOS 11.5.2 follows macOS 11.5.1 (which contained security updates) and macOS 11.5 (which also consisted largely of—you guessed it—bug fixes and security updates). We probably won't see significant new macOS features until macOS Monterey arrives later this year.
Among other things, that major upcoming release is expected to include various new ways to integrate a Mac with an iOS or iPadOS device, like Universal Control. This will facilitate new ways of controlling macOS and iPad devices together with the same mouse and keyboard.
3. Netflix is adding residential IP addresses to its VPN blocklists
Netflix's new "VPN" block policies can catch innocent users in the crossfire.
by Jim Salter
The privacy and access wars waged between consumers and content providers don't seem likely to abate any time soon.
Netflix blocks known commercial VPNs and proxies from accessing its services in order to preserve its geofencing—partitioning access to content based on a user's real-world location. Users who connect to a commercial VPN or proxy provider endpoint in another country can access content licensed for viewing in the endpoint country—but not in the viewer's own.
Recently, as reported by TorrentFreak, Netflix began including putatively residential IP subnets in its blocklists.
Cat and mouse
Since Netflix first began blocking commercial VPN and proxy providers in 2015, those services have fought back by finding ways to evade its and other streaming services' blocking attempts.
The simplest way is just to discard an existing subnet that's been widely identified as "VPN/proxy" and purchase another, "clean" space. This move can buy a blocklist evader a few days or even weeks before the new subnet is added to the list.
This basic conflict between VPN providers eager to keep region-shifting customers happy and streaming services trying to keep content licensers pacified led to a six-year-long cat-and-mouse game. Both sides are pretty cagey about the technical details, but one technique the VPN providers use is leasing IP addresses in supposedly "residential" IP subnets to use as exit proxies.
One commercial VPN provider told TorrentFreak that recently, Netflix began blocking those "residential" proxy addresses as well—with some readily apparent collateral damage. "You have hundreds of thousands of legitimate residential Netflix subscribers blocked," WeVPN's spokesperson said.
Scope of damage
Falling afoul of Netflix's VPN block doesn't hurt quite as badly these days as it did in 2015. Instead of an outright ban on devices coming from a blocked IP address, the service now somewhat selectively removes access to region-locked content.
If you want to watch Netflix originals across a VPN, you can do so whether your endpoint is on the service's blocklist or not, but region-locked content will be hidden from view, neither browsable nor playable. A clever user who tries to access hidden content using a deep link directly to that content gets a "Pardon the interruption" error dialog asking the user to turn off VPNs and proxies instead.
Although WeVPN claims "hundreds of thousands of users" who don't use VPNs or proxies have been caught in the crossfire, the real numbers aren't yet clear. Some Redditors report "missing content" when accessed over Wi-Fi, with the same content showing up again on mobile data. This situation corresponds to Netflix's current VPN blocklist policies. A similar user report on Twitter got an odd response from Netflix pointing the finger right back at the user's ISP:
Hi Raymond, help is here! If you do not have proxies, VPNs, or other routing software but still see this message, contact your internet service provider. They'll be able to determine why your IP address is associated with proxy or VPN use.
Some tech-savvy Netflix users have reported working around the false-block issue by releasing their public IP address and getting a new one—but that approach only helps if you know what you're doing, your ISP issues DHCP addresses, and the lease on those addresses is relatively short.
We aren't very optimistic about outcomes for customers who don't meet all those criteria and are stuck calling into ISP support departments not primed for this sort of call
Contact please for any suggestions
4. Xiaomi clones the iPad Pro for half the price: $386
Xiaomi is the latest company to show renewed interest in Android tablets.
by Ron Amadeo
Xiaomi
The Xiaomi Mi Pad 5 Pro, definitely using a design that has never been used before, especially not by any fruit-named companies.
Android tablets are totally coming back, right? Google has launched a few tablet apps lately after years of neglect, it gave talks at Google I/O on how to design tablets apps, and the Android 12 developer preview shows that the company is working on a taskbar-like UI for big-screen devices. Now, the world's most popular Android device manufacturer, Xiaomi, is releasing an Android tablet for the first time in three years.
We're suckers for these internal pictures.
The Xiaomi Mi Pad 5 Pro seems just a little inspired by Apple's flagship tablet, the iPad Pro. Xiaomi regularly produces wild, technology-packed designs, but at times, it also falls back into its old ways of being an Apple clone manufacturer. This is one of those times.
The company's new tablet has an 11-inch, 120 Hz, 2560×1600 LCD and is relatively high-end, with a Snapdragon 870 SoC (that's a 7 nm chip with four Cortex A77 cores and four Cortex A55 cores).
The base unit comes with 6GB of RAM and 128GB of storage, with options for 8GB of RAM and 256GB of storage. There's an 8600 mAh battery, NFC, a side fingerprint reader/power button, Wi-Fi 6 support, a USB-C port, and a whopping eight speakers, all split between the left and right sides. The frame and back are both aluminum, and the tablet weighs 515 g.
Why on earth is the front camera on the side of the device? This will be on the left side with the keyboard attached.
The one part of the design you could complain about is the front camera, which is on the left side of the device in landscape mode, so it's not very useful for landscape video calls. The placement is especially strange because the keyboard accessory, side speakers, and side fingerprint reader all encourage landscape use as the primary mode. The reason for the odd camera location might be support for the pen accessory, which uses the top edge of the tablet (in landscape) to magnetically attach and wirelessly charge.
Cloning Apple is certainly a bad Xiaomi habit, but the company is also keeping its good habits—namely, releasing decent hardware for low prices. The Mi Pad 5 Pro starts at CNY 2,499 (~$386), or about half the price of the entry-level 11-inch iPad Pro, which is $799.
There's also a cellular version with a presumably better primary rear camera (50MP versus 13MP), the Mi Pad 5 Pro 5G, which clocks in at about $540—still around half the price of the $1,000 cellular iPad Pro. Xiaomi is also selling iPad-style accessories, like a keyboard for about $62, which is way cheaper than the $300 Magic keyboard for the iPad.
A stylus sells for about $62, smoking the $129 Apple Pencil when it comes to price. There are probably a million ways the iPad Pro is faster and more polished than Xiaomi's offering, but for half the price, many consumers will consider it close enough.
For now, all these prices are converted from CNY, since the device is currently only sold in China. That's where all Xiaomi devices start out, though, and they usually get wider rollouts.
5. Calculator, Mail, other built-in apps get a Windows 11 facelift in latest beta
Microsoft continues to freshen up apps while snipping out duplicative features.
by Andrew Cunningham
Enlarge / Get excited! The new Calculator app is here!!
Andrew Cunningham
Microsoft is giving the Windows 11 treatment to a handful of core apps in the next Insider Preview build of the upcoming operating system. Mail, Calendar, the Calculator, and the Snipping Tool are all being revamped, and if you're running the latest Insider Preview, you should be able to grab these updates from within the Windows Store app starting today.
The changes in Mail, Calendar, and Calculator appear to be largely cosmetic, ejecting the squared-off corners of Windows 8 and 10 for a softer, more rounded look that fits in with the rest of the operating system.
The one "new" app is a revamp of the Snipping Tool that unifies the features of the old Snipping Tool and the Windows 10 Snip & Sketch app (this update brings the useful side effect of finally getting rid of the annoying message telling you that the Snipping Tool is going away every time you open it up).
Microsoft
The new Snipping Tool updates its predecessor's Windows 7-era UI while integrating the features of Windows 10's duplicative Snip & Sketch tool.
The new Snipping Tool still gives you buttons for changing what kind of screenshot you're trying to take and whether you want it to happen on a delay. Its annotating tools for screenshots have been given a more modern facelift, too (the old ones were stuck in the Windows 7 era). Snip & Sketch users can continue to access that handy UI by using the Windows + Shift + S keyboard shortcut.
The new apps will roll out to Windows Insiders on the less-stable Dev Channel first. Microsoft began releasing Windows 11 builds to the more-stable Beta Channel in late July, and you'll need to keep waiting if you want to use these new features on a less bleeding-edge iteration of Windows. You can always change your channel from the Windows Update section of the Settings app.
As with all Insider Preview builds so far, Microsoft is not enforcing Windows 11's new security requirements just yet, so most computers that run Windows 10 will still be able to run new Windows 11 builds and these updated apps.
6. Samsung's chief is out of prison, permitting US production line intends to push ahead
Samsung beneficiary served year and a half in jail for capital flight and prevarication.
by Ron Amadeo
Jay Y. Lee, head of Samsung Gathering, addresses individuals from the media as he is delivered from the Seoul Confinement Center in Uiwang, South Korea.
Samsung Gathering's chief, Jay Y. Lee, is out of prison on parole today. Lee was carrying out a 30-month punishment for his job in "Choi-door," a significant 2016 South Korean political embarrassment that cut down South Korean then-President Park Geun-hye.
In 2017, Lee was initially condemned to five years in prison in the wake of being seen as liable of pay off, theft, capital flight, and prevarication. An allure and retrial cut Lee's five-year jail sentence down to 30 months in the wake of suspending the charges for pay off and theft. Lee carried out year and a half of that punishment, and presently he's free from jail, but still under watch.
Choi-entryway is an inconceivable hare opening you can jump into at the above Wikipedia connect, yet so, it's named for Choi Soon-Sil, a shamanistic clique part and a lady frequently called "Korean Rasputin," because of her impact over South Korea's then-president. Lee was blamed for paying off Choi to get a positive decision from Park identified with a 2015 consolidation of two Samsung subsidiaries, Samsung C&T Corp (that is "Development and Exchanging") and Cheil Businesses, a Korean material firm.
Upon his delivery, Lee told correspondents, "I've caused a lot of worry for individuals. I profoundly apologize. I'm paying attention to the worries, reactions, stresses, and elevated requirements for me. I will buckle down."
Lee's delivery from jail is disputable. The supportive of business side of South Korean legislative issues needs to see Lee back on the roads on the grounds that Samsung is a gigantic piece of South Korea's economy, and imprisoning the pioneer has postponed major vital choices at the organization. Municipal gatherings say South Korea's business world class get an alternate arrangement of rules from every other person and that Lee's parole is the most recent indication of that reality.
South Korean President Moon Jae-in's office delivered a proclamation on Lee's delivery, saying, "We are very much aware that there are supporting and restricting perspectives on Bad habit Executive Jay Y Lee's parole.
The perspectives on individuals who are gone against are likewise correct. Then again, there have been many individuals who required his parole in this serious emergency, trusting that he will assist the country as for semiconductors and antibodies."
Samsung makes up somewhere in the range of 10-20 percent of South Korea's Gross domestic product, contingent upon how the most recent quarter is going. As the big enchilada at Samsung, Lee has the last say on significant speculations and acquisitions, and one of the critical choices he needs to make is the place where to assemble a $17 billion chip plant in the US.
The plant could be functional when October 2022, and with the world presently in the center of a worldwide chip lack, there's strain to kick everything off. US organizations have even been campaigning South Korea to exculpate Lee in the expectations that the arrangement would go through.
Lee allegedly left jail to make a beeline for Samsung base camp, however he actually has more lawful issues to manage. In October, he will confront another preliminary identifying with the Samsung C&T consolidation, this time for bookkeeping extortion and stock value control.
7. A straightforward programming fix could restrict area information sharing
With Very Great Telephone Protection, transporters wouldn't generally know where you are.
by Lily Feed Newman, wired.com
Very Great Telephone Security needs to limit how much your remote supplier thinks about your area.
Area information sharing from remote transporters has been a significant protection issue as of late. Advertisers, salesmen, and even abundance trackers had the option to pay shadowy outsider organizations to follow where individuals have been, utilizing data that transporters assembled from cooperations between your telephone and close by cell towers.
Even subsequent to promising to quit selling the information, the significant transporters—AT&T, T-Versatile, and Verizon—purportedly proceeded with the training in the US until the Government Correspondences Commission proposed almost $200 million in consolidated fines. Transporters remain lastingly hungry to know as much about you as possible. Presently, analysts are proposing a basic intend to restrict how much mass area information they can get from cell towers.
A large part of the outsider area information industry is energized by applications that acquire consent to get to your GPS data, however the area information that transporters can gather from cell towers has regularly given an elective pipeline. For quite a long time, it's seemed like little should be possible about this spillage since removing admittance to this information would almost certainly require the kind of fundamental redesigns that transporters are unwilling to make.
At the Usenix security gathering on Thursday, however, network security scientists Paul Schmitt of Princeton College and Barath Raghavan of the College of Southern California are introducing a plan considered Very Great Telephone Protection that can cover remote clients' areas from transporters with a straightforward programming redesign that any transporter can take on—no structural foundation shifts required.
"The essential issue we're attempting to address is mass information assortment and its offer," Raghavan says. "We consider it to be a client security issue that transporters can hoard this area information whether they are as of now effectively selling it. Also, our objective here was in reverse similarity. We didn't need the telecoms to need to carry out anything since we realized they weren't going to."
The chance to gather mass area information from remote organizations emerges from the way that each SIM card has a super durable ID number, known as an "worldwide portable supporter personality," or IMSI number. At the point when your gadget reboots, has been inert for some time, or simply needs to build up a new association, it contacts the closest cell pinnacle and presents an IMSI number.
This permits transporters to check whether you've covered your telephone bill and ought to be permitted admittance to administration, and it likewise tells the organization which cell towers you're near. Observation devices known as "stingrays" or "IMSI catchers" exploit this equivalent association to snatch your actual area and even listen in on your calls and messages.
To make it more hard to follow you constantly, remote principles as of now allocate every gadget an arbitrary, turning ID after the underlying IMSI trade. This implies that there are as of now a few assurances incorporated into the framework; making that first IMSI step more private would have broad advantages for clients.
Very Great Telephone Security, whose name is a gesture to the noteworthy 1991 correspondence encryption program Very Great Protection, means to accomplish only that by reconsidering the charging watch that organizations perform. The scientists propose introducing entrances on each gadget—utilizing an application or working framework work—that run customary checks with a charging worker to affirm that a client is on favorable terms.
The framework would give out advanced tokens that don't recognize the particular gadget yet essentially demonstrate whether the joined remote record is settled up. At the point when the gadget endeavors to interface with a cell tower, the trade would pipe through this entryway for a "yes" or "no" on whether to offer support. The analysts further understood that if the framework has a substitute strategy for affirming charging status, it can acknowledge a similar IMSI number or any arbitrary ID for every client.
"At the point when you join to the organization, you offer the IMSI number to show the backend information base that you are a paying client, and here are the administrations that you have bought in to," Schmitt says.
"The framework then, at that point advises the rest regarding the center to permit you onto the organization. However, how we manage PGPP changes the math. The endorser information base can check that you're a paying client without knowing what your identity is. We've decoupled and moved charging and validation."
Revising some charging frameworks and circulating an application to clients would be definitely more reasonable for transporters than more profound organization upgrades. Raghavan and Schmitt are currently transforming their examination into a startup to make advancing the undertaking simpler among US telecoms. They recognize that even effortlessly of reception, it's as yet a remote chance that the entire business would move to PGPP at any point in the near future. Be that as it may, getting a couple of transporters, they say, could in any case have a major effect.
That is on the grounds that mass area information turns out to be considerably less solid if any critical piece of the complete set is spoiled. In the event that 9 million Lift Versatile supporters, for example, were to communicated indistinguishable or randomized IMSI numbers, that would sabotage the precision and value of the whole informational collection.
The way that little, virtual suppliers who don't work their own cell towers—known as MVNOs—could carry out this plan freely is critical, says cryptographer Bruce Schneier, who initially found out about PGPP in January and has as of late become a venture consultant.
"One transporter can do it all alone without anyone's consent and without any other person evolving anything," Schneier says. "I can envision one of these more modest organizations saying they will offer this as a worth add since they need to separate. This is security at very little expense. That is the flawless thing."
In the serious, solid remote market, standing separated on protection could be engaging as a showcasing strategy. It's conceivable that the enormous three transporters could endeavor to hinder MVNOs from taking on something like PGPP through authoritative moratoria. However, the specialists say that some MVNOs have communicated interest in the proposition.
Between expected pressing factor from law requirement and loss of information access—in addition to the need to circulate an application or get versatile working frameworks to take part—transporters could have minimal motivating force to take on PGPP. To the degree that law implementation may go against such a plan, Schmitt takes note of that it would in any case be feasible for transporters to perform designated area history queries for explicit telephone numbers. What's more, the specialists say they accept the methodology would be legitimate in the US under the Correspondences Help for Law Requirement Act.
This is on the grounds that one proviso of PGPP is that it just adds security assurances for cell tower associations that include information networks like 4G or 5G. It doesn't endeavor to interoperate with the memorable communication conventions that work with customary calls and SMS instant messages. Clients would have to depend on VoIP calling and information based informing for greatest security.
The methodology likewise centers around IMSI numbers, alongside their 5G partners known as Membership Long-lasting Identifiers, or SUPI, and it doesn't secure or block static equipment identifiers like Worldwide Portable Hardware Personality (IMEI) numbers or media access control (Macintosh) addresses. These aren't utilized in the cell tower cooperations the scientists are attempting to anonymize, however they could give different roads to following.
Having a basic and clear alternative to address one significant area information openness is as yet huge, however, following quite a while of information abuse and rising protection concerns.
"Just cutting straight to the chase, the inclination for me presently is, the manner by which did we not see this previously?" Raghavan says. "It's not, 'Goodness, this was so hard to sort out.' It's undeniable by and large."
"That really helped us in general as frameworks scientists," Schmitt adds. "Eventually, the more straightforward the framework, the better the framework.
8. The Perl Foundation is fragmenting over Code of Conduct enforcement
"I'm fresh out of ideas with regards to handling toxicity in the Perl community."
by Jim Salter
One of the Perl programming language's best-loved nicknames is "the Swiss Army chainsaw." The nickname also seems unfortunately applicable to Perl's recent community discourse.
The Perl Foundation is in a shambles due to disputes concerning its (nonexistent) Code of Conduct, its (inconsistent) enforcement of community standards, and an inability to agree on what constitutes toxicity or a proper response to it.
At least four prominent Perl community members have resigned from their positions at the Perl Foundation recently, and another has withdrawn from working on Perl entirely:
Community Affairs Team (CAT) chair Samantha McVey
The Perl Foundation (TPF) Board of Directors member Curtis Poe (author of Beginning Perl and Perl Hacks)
TPF Grant Committee member Elizabeth Mattijsen
Perl developer and SUSE engineer Sebastian Riedel
Perl Steering Council member, key Perl Core developer, and former pumpking Sawyer X
It's difficult to impossible to pin down the current infighting to a single core incident. With that said, the rash of resignations revolves entirely around problems with unprofessional conduct—problems exacerbated by a focus on interminable yak-shaving that does little or nothing to address the actual problems at hand.
Sawyer X (resigned April 12)
Perl Core developer and "pumpking" (roughly meaning elected manager of the entire Perl language) Sawyer X resigned from the Perl Steering Council and Perl Core in April, claiming an intolerable barrage of hostile messages from Perl community members. Sawyer cites responses to a message saying "there is cruft in [Perl]" as the excuse some Perl community members used to "push him into a corner" until he deactivated his Twitter account.
In the crucial thread, developer Matthew Trout dismissively states, "The people actually doing the work on perl core don't seem to find the 'cruft' problematic." After some back and forth over who does or does not count as a Perl maintainer who might object to cruft, Sawyer declares, "I have no interest in discussing anything with you, Matt."
To an outsider, the thread seems quite tame, even reasonably polite. Only Sawyer's refusal to continue discussion with Trout hints at the real distress underneath—which might have something to do with the reasons Trout was permanently banned from Perl events a week later.
Trout's ban was due in part to 2019 conference behavior that fellow developer Aaron Crane described elusively as philosemitic antisemitism—and in part to unspecified "ongoing behavior" from Trout that makes other community members uncomfortable. The Board later reviewed the CAT's actions, deleted its "transparency" reports, and changed Trout's permaban to a one-year ban.
Trout, for his part, later told The Register that he was upset about having hurt Sawyer and that he accepted the revised one-year ban as "the best thing for [Trout's] friends and community."
Sebastian Riedel (resigned June 25)
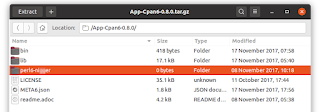
Enlarge / Yes, this Spek-authored folder says what you think it does—and it's still available for download from Perl's CPAN software archives.
Jim Salter
In March of this year, Patrick Spek—a former member of the Perl 6 (Raku) steering council—committed to .config/git/config with a commit message saying "Get a job" followed by the n-word. Sebastian Riedel lodged a complaint with TPF board, which he says was railroaded by a board member—therefore, Riedel quit.
Riedel's complaint to the board points out that this isn't Spek's first racism rodeo. CPAN still offers downloads containing a 2017-era tarball from Spek with a folder named "perl6-n[word]". We downloaded the linked file and can verify that it's still available from CPAN, and it does in fact contain that folder.
Making matters worse, Riedel alleged that McVey—who headed up the CAT and thus was responsible for responding to the incidents in question—was romantically involved with Spek at the time.
Update: After this article published, Riedel clarified that his frustration is with TPF specifically, tweeting "the broader Perl Community has absolutely no influence on the Perl Foundation. The Foundation is governed by cronyism and there is nothing a normal Perl developer can do about it."
Samantha McVey (resigned Aug. 7)
At the time of her resignation, Samantha McVey chaired TPF's Community Action Team (CAT). McVey cited her resignation as primarily due to TPF Board's failure to pass a Charter and Code of Conduct, along with the board's decision to unilaterally revoke (and delete) all CAT transparency reports issued in 2021.
"Retracting the CAT’s transparency reports sends the message the Board of Directors is not willing to support the CAT, and is not prioritizing the safety of the community," McVey said. She added that she was not involved in the board's decision to retract the reports—and that if she were not to resign, it would appear she supports the board's actions.
Although McVey's resignation primarily cited her perception of the board's inability to lead and lack of transparency, she seems to share a general frustration with the Perl community with others who resigned.
McVey's position in Perl's struggles is complicated by Riedel's allegations that she was romantically involved with Spek (who has a history of undeniably racist language and commits) and that she was indifferent to reports of Spek's use of the "n-word" in messages and code commits. That's conduct one assumes would flagrantly violate the Code of Conduct McVey submitted to the board in the first place.
Update: McVey reached out to clarify: "I am no longer involved romantically with Patrick Spek due to his past actions."
Elizabeth Mattijsen (resigned Aug. 7)
TPF Grant Committee member Elizabeth Mattijsen resigned on the same day as board member Samantha McVey, citing TPF Board's decision to put the CAT on hiatus and retract its former reports as "the last straw."
Mattijsen said she was already considering resignation before the CAT hiatus, due to the board failing to confirm funding for already approved grant requests. "TPF has not published anything about their financial state ever," Mattijsen told one Twitter commenter. She added that "the chair of the Grant Committee was told to wait for the treasurer to return from vacation, to find out whether grants were to be funded. Which I found VERY odd."
Later, Mattijsen proffered a Reddit r/Perl comment accusing McVey of being at the center of some shadowy cabal as "an example of the kind of toxicity that made me leave the Perl community."
Curtis Poe (resigned Aug. 9)
On Github, Poe categorizes his resignation from TPF Board as due to "burnout"—"I stopped reading the meeting minutes. And that's when I realized I was burned out. Or burnt out. Or whatever. I just didn't care."
Poe names various controversies over the Community Affairs Team—its actions and lack thereof, the community's reactions to that, the CAT's response to those, and so forth—as key to his final decision, though he is reticent to explain more concretely.
"If you don't understand the following, consider yourself lucky. I've no desire to explain this mess," Poe writes. Although Poe refuses to go into much detail, he appears to be referring to the then-ongoing strife between Sawyer X and developer Matt Trout, which ultimately led to Sawyer's exodus from Perl.
Conclusions
After spending a day wading through the stated reasons and back stories of these high-profile resignations, it's difficult to come to any single, clear conclusion—although "burn this entire pile of serpents down, with the most primal of magics" is frankly tempting.
I have personally used and enjoyed the Perl language for nearly 30 years, and it's distressing to see the bigotry and edgelording coming from prominent elements of the community—not to mention the board's failures to respond decisively. The Perl community is not the first to struggle with "culture wars" revolving around a code of conduct, either, which makes it all the more puzzling why its board seems incapable of formulating one.
Ultimately, the presence of toxic elements—whether racist, sexist, or just plain aggressive bullying—in a community of any real size is perhaps inevitable. The real test of a community is not the discovery of those elements, but its reaction to them—particularly its willingness to acknowledge them. So far, the Perl community seems to be failing that test.
9. Audit: Androids is a designer analysis track for the Android 1.0 time
Another book by Googler Chet Haase offers an inside take a gander at Android improvement.
by Ron Amadeo
Many Android colleagues were met for the book, I can just accept it resembled this.
Android will stand out forever as quite possibly the main programming projects ever. Today, there are a dumbfounding three billion month to month dynamic Android gadgets, and that number gets greater consistently. The operating system advocated the manner in which we get versatile notices, spearheaded the cutting edge application store model, and essentially killed the whole close to home GPS industry when it dispatched Google Guides route.
As Ars' inhabitant Android Student of history, I was excited to hear that Chet Haase, a long-lasting individual from the Android group inside Google, was composing a book itemizing the beginning of Android improvement. We make an honest effort to record Android from an external perspective, yet it's nothing contrasted with what the real engineers could advise us.
Androids: The Group that Constructed the Android Working Framework is Haase's new book, and it's loaded with down and dirty stories from individuals that made Android. Haase has been in the Android group since 2010, and he has pretty consistently been a significant course between general society and whatever the Android group is dealing with.
He frequently makes that big appearance at Google I/O to co-have what is essentially the Android Condition of the Association address: the "What's happening in Android" talk, which subtleties all the new engineer declarations. He co-has the week after week "Android Designers Behind the stage" digital recording, and afterward there's his normal everyday employment as a genuine architect in the Android illustrations group.
Androids: The Group that Assembled the Android Working Framework
[by Chet Haase]
$10 AT AMAZON
$10 AT GOOGLE PLAY
Since Haase is in the Android group, he normally has phenomenal admittance to the Android group, and his book highlights many Android colleagues on the record portraying what the good 'ol days resembled. Haase and the group had the option to uncover a lot of old pictures as well, so all through the book you'll see Android engineers working at immediately put together stations, huge loads of testing hardware, and odd exploratory models.
Androids is a secret stash of data. While all of at present open early Android data has been inventoried to death on the Web (my pleasure), many pages of this book nonchalantly doles out at no other time seen Android data. Assuming you need a preference for yourself, we re-distributed parts four and five of the book, and those two sections alone contain an image of an early Android demo on a Cingular flip telephone (Cingular would go on to rebrand itself "AT&T Remote" in 2007), a piece of the Android Inc financial backer introductions, and data about the Google buyout.
Practically none of that has been public previously, and the entire book is this way. It is inconsiderate to strip dig the whole book for data, yet Androids could uphold a long time of stories in the tech consistent pattern of media reporting, or patches up of a few Wikipedia articles to say the least. (On the off chance that any of you Android individuals out there have a greater amount of this stuff, if it's not too much trouble, share!)
The book covers the pre-Google Android Inc. time when the organization was pitching a camera operating system to VCs, Android Inc's obtaining by Google, and the approach the Android 1.0 dispatch. It just at times steps further into the future than that. The early parts are only a flood of wistfulness for old tech-heads.
The book portrays the 2006-period Android group as a blend of veterans of Android fellow benefactor Andy Rubin's past organizations—Risk Inc and Microsoft's WebTV division—alongside individuals from Palm and its obtaining of BeOS. There was a huge load of involvement building working frameworks in the organization, and in the good 'ol days, the group wasn't generally in total agreement when it came to significant plan choices. Groups inside the Android group frequently separated generally along the business history lines: Risk versus BeOS/PalmSource versus Microsoft/WebTV. Whose method of doing things should win out? Should the group fabricate a firmly perused item or a more adaptable stage? Ought to applications be written in C++ or Java? How confounded ought to performing multiple tasks and application to-application correspondence be?
Like it says on the tin, the book is particularly about the distinctive individuals who fabricated Android. You'll get profiles and histories for the colleagues of every Android division, figure out how they discovered their approach to Android, and partake in a portion of their individual conflict stories and office shenanigans from when they dealt with the operating system.
On the off chance that you at any point watch designer recordings like the Google I/O fireside visits, you'll see a great deal of natural names, including regular Ars interviewees like Dave Burke and Iliyan Malchev. It's likewise enjoyable to hear the whole staff's love for Android Structure engineer Dianne Hackborn, portrayed in the book as "a superhuman." Maybe the greatest commendation you can give, she was the principal individual Haase met for the book.
The Android group expected to move at an amazing speed in the early years, since it was hustling to prevent the iPhone from assuming control over the world. A ton of the conflict stories from that point are inconceivable. A couple of top picks are that the dispatch gadget, the HTC T-Portable G1, had a sound driver that would crash in the event that you attempted to play different sound documents on the double. So an Android subsystem called "AudioFlinger" was hurriedly kept in touch with gather up every one of the approaching sound asks for and combine them into a solitary sound stream, which was sufficient to keep the little dispatch gadget running.
Another jewel is that a testing script called "Monkey" would arbitrarily tap on UI components to chase down slamming bugs, however one day somebody came into the workplace to discover the content had dialed 911. Hackborn added the capacity "isUserAMonkey()" to Android's action director to prevent the testing script from doing unfortunate activities like this, yet the bizarre name and brassy documentation made this a typical wellspring of inquiries in the Android people group.
However in case we're being straightforward, I'm as yet not certain in case there are any genuine uses for "isUserAGoat()" in the client supervisor or why the sensor director has an incentive for gravity on the Passing Star. (I suspect these are additionally the flaw of the BeOS public.)
It was additionally intriguing to find out about the Android group's place inside Google. In the good 'ol days at the inquiry goliath, Android was cryptic to the point that it would need to enroll individuals prior to mentioning to them what Android was really doing.
A few group that moved from Google portray how unique the way of life was, and how Android wanted to move to another organization, despite the fact that it was important for Google. A portion of that culture appears to make due right up 'til today, with late ex-Googlers like Steve Yegge additionally portraying Android like it was an absolutely discrete organization.
Androids: The Group that Fabricated the Android Working Framework is marked down now at different book shops. In case you're the sort that pays attention to chief discourse tracks on a film, this is essentially that, however for Android 1.0 and prior. It's a pleasant read for tech nerds and actually the best way to get an in the background see what creating Android resembled.
10. Samsung has its own AI-designed chip. Soon, others will too
Semiconductor software-design maker Synopsys is adding AI to its arsenal.
by Will Knight, wired.com
Samsung is using artificial intelligence to automate the insanely complex and subtle process of designing cutting-edge computer chips.
The South Korean giant is one of the first chipmakers to use AI to create its chips. Samsung is using AI features in new software from Synopsys, a leading chip design software firm used by many companies. “What you’re seeing here is the first of a real commercial processor design with AI,” says Aart de Geus, the chairman and co-CEO of Synopsys.
Others, including Google and Nvidia, have talked about designing chips with AI. But Synopsys’ tool, called DSO.ai, may prove the most far-reaching because Synopsys works with dozens of companies. The tool has the potential to accelerate semiconductor development and unlock novel chip designs, according to industry watchers.
Synopsys has another valuable asset for crafting AI-designed chips: years of cutting-edge semiconductor designs that can be used to train an AI algorithm.
A spokesperson for Samsung confirms that the company is using Synopsys AI software to design its Exynos chips, which are used in smartphones, including its own branded handsets, as well as other gadgets. Samsung unveiled its newest smartphone, a foldable device called the Galaxy Z Fold3, earlier this week. The company did not confirm whether the AI-designed chips have gone into production yet, or what products they may appear in.
Across the industry, AI appears to be changing the way chips are made.
A Google research paper published in June described using AI to arrange the components on the Tensor chips that it uses to train and run AI programs in its data centers. Google’s next smartphone, the Pixel 6, will feature a custom chip manufactured by Samsung. A Google spokesperson declined to say whether AI helped design the smartphone chip.
Chipmakers including Nvidia and IBM are also dabbling in AI-driven chip design. Other makers of chip-design software, including Cadence, a competitor to Synopsys, are also developing AI tools to aid with mapping out the blueprints for a new chip.
Mike Demler, a senior analyst at the Linley Group who tracks chip-design software, says artificial intelligence is well suited to arranging billions of transistors across a chip. “It lends itself to these problems that have gotten massively complex,” he says. “It will just become a standard part of the computational tool kit.”
Using AI tends to be expensive, Demler says, because it requires a lot of cloud computing power to train a powerful algorithm. But he expects it to become more accessible as the cost of computing drops and models become more efficient. He adds that many tasks involved in chip design cannot be automated, so expert designers are still needed.
Modern microprocessors are incredibly complex, featuring multiple components that need to be combined effectively. Sketching out a new chip design normally requires weeks of painstaking effort as well as decades of experience. The best chip designers employ an instinctive understanding of how different decisions will affect each step of the design process. That understanding cannot easily be written into computer code, but some of the same skill can be captured using machine learning.
The AI approach used by Synopsys, as well as by Google, Nvidia, and IBM, uses a machine-learning technique called reinforcement learning to work out the design of a chip. Reinforcement learning involves training an algorithm to perform a task through reward or punishment, and it has proven an effective way of capturing subtle and hard-to-codify human judgment.
The method can automatically draw up the basics of a design, including the placement of components and how to wire them together, by trying different designs in simulation and learning which ones produce the best results. This can speed the process of designing a chip and allow an engineer to experiment with novel designs more efficiently. In a June blog post, Synopsys said one North American manufacturer of integrated circuits had improved the performance of a chip by 15 percent using the software.
Most famously, reinforcement learning was used by DeepMind, a Google subsidiary, in 2016 to develop AlphaGo, a program capable of mastering the board game Go well enough to defeat a world-class Go player.
De Geus says his company realized that reinforcement learning could also be useful for chip design. “A bit over a year and a half ago, for the first time, we were able to get the same results as a team of experts would get in multiple months in just a few weeks,” de Geus says. He will present details of the technology and its development at HotChips, a semiconductor technology conference, on August 23.
Stelios Diamantidis, senior director of artificial intelligence solutions at Synopsys, says the DSO.ai software can be configured to prioritize different goals, such as performance or energy efficiency.
Semiconductors, as well as the tools used to make them, have become increasingly prized assets. The US government has sought to restrict the supply of chipmaking technology to China, a key rival, and some politicians have called for software to be added to the export controls list.
The emerging era of AI-designed chips also raises the prospect of simultaneously using AI to customize software to run more efficiently on a chip. This might include the neural network algorithms that run on specialized AI chips and are commonly used in modern AI.
“AI-powered codesign of software and hardware is a rapidly growing direction,” says Song Han, a professor at MIT who specializes in AI chip design. “We have seen promising results.”
11. Intel’s Arc GPUs will compete with GeForce and Radeon in early 2022
"Alchemist" will be Intel's first serious dedicated gaming GPU.
by Andrew Cunningham
The brand name for the Intel GPU formerly known as "DG2."
Intel
Intel has been working for years to enter the high-end graphics card market to compete with Nvidia and AMD, and today those efforts get a name: Intel Arc (not to be confused with Intel Ark, the site you go to when you need help with Intel's indecipherable processor model numbers). The earliest Arc products will be released in "the first quarter of 2022" and will be based on a GPU codenamed "Alchemist," a new, more memorable codename for a GPU previously known as "DG2."
The first Arc cards will be a follow-up of sorts to DG1—a card released only to system builders—which performs a lot like the GDDR5 version of Nvidia's aging, low-end GeForce GTX 1030.
We don't have spec sheets for any of the Alchemist-based Arc cards yet, but the trailer Intel showed confirmed support for modern GPU features like real-time ray tracing and "AI Accelerated Super Sampling" that will compete with Nvidia's DLSS and AMD's FidelityFX upscaling technologies. The trailer also showed Arc silicon running real (if somewhat older) games like Forza Horizon 4 and Metro Exodus.
To demonstrate its commitment to the discrete GPU market, Intel announced several more GPU codenames that will succeed Alchemist in the coming years, including "Battlemage," "Celestial," and "Druid" (note both the alphabetical order and the high-fantasy theme).
Arc will represent Intel's first serious run at the gaming GPU market, but the company isn't starting from zero. The company has decades of experience in writing and updating graphics drivers, and it is in the habit of releasing both "stable" driver packages and beta drivers with improvements for specific games, much like AMD and Nvidia already do. And while it doesn't blow the doors off of AMD's integrated GPUs in its Ryzen APUs, the Intel Iris Xe graphics in 11th-generation Core laptops can actually run many games at 1080p or 720p.
We don't know anything about performance, pricing, or availability for any Arc cards yet, but if the current GPU shortage extends into early 2022, it will present a unique opportunity for Intel—gamers desperate to get their hands on any reasonably competent GPU will be more inclined to take a chance on an Intel card than they might otherwise be.
Even relatively lackluster cards like Nvidia's RTX 3060 and AMD's 6600 XT have been quick to sell out in the current market, so as long as Alchemist doesn't set your computer on fire, it stands a reasonable chance of success.
12. Sonos gets early patent triumph against Google shrewd speakers
The fundamental decision could prompt a restriction on Home Sound, Pixel, and Chromecast.
by Ron Amadeo
Sonos says the Google Home took its innovation.
Jeff Dunn
Sonos scored an early triumph for its situation against Google Friday, when the US Worldwide Exchange Commission decided that Google encroached five of Sonos' keen speaker licenses. The decision is fundamental and dependent upon a full ITC survey, however it could prompt a restriction on Google keen speakers.
In January 2020, Sonos brought a patent encroachment body of evidence against Google focusing on Google's keen speakers, the Google Home, and later the Home Sound line. Sonos is the originator of Web associated speakers that effectively attach to web-based features, while Google speakers join a comparable list of capabilities with voice-actuated Google Collaborator orders.
To hear Sonos recount the story, Google got an in the background take a gander at Sonos' equipment in 2013, when Google consented to construct Google Play Music support for Sonos speakers. Sonos claims Google utilized that admittance to "conspicuously and intentionally" duplicate Sonos' sound components for the Google Home speaker, which dispatched in 2016.
Anyway you need to gauge it, Sonos is a minuscule organization contrasted with the tech monsters it consistently fights. The 19-year-old organization just has items in the associated speaker market, and it has a $5 billion market cap. Its rivals—Google, Amazon, and Apple—are a portion of the world's greatest organizations, each with a market cap above $1.5 trillion.
To make matters more convoluted for Sonos, the organization depends on both Google and Amazon to work together in search, promoting, and retail deals, and it stressed over reprisal from the two goliaths. Besides, when Amazon and Google entered the market, Sonos had to take on help for both voice partners to contend. Back in 2020, Sonos said Amazon likewise appeared to utilize its innovation, yet it would zero in its lawful endeavors on Google.
TechCrunch got articulations from the two sides of the battle. First up, Sonos Boss Legitimate Official Eddie Lazarus told the site, "Today the ALJ has observed to be every one of the five of Sonos' declared licenses to be substantial and that Google encroaches on each of the five licenses.
We are satisfied the ITC has affirmed Google's outright encroachment of Sonos' protected creations. This choice re-confirms the strength and expansiveness of our portfolio, denoting a promising achievement in our drawn out pursuit to safeguard our advancement against misappropriation by Enormous Tech syndications."
In the interim, Google said, "We don't utilize Sonos' innovation, and we contend on the nature of our items and the benefits of our thoughts. We can't help contradicting this fundamental decision and will keep on presenting our defense in the impending audit measure."
A last decision ought to occur on December 13, and not simply speakers could be prohibited if the two organizations don't get along. The items that associate with those speakers, similar to Pixels and Chromecasts, could likewise be closed down.←→
13. The long-awaited M1X MacBook Pro will be here by November, reporter claims
Despite production delays, the M1X or M2 Macs are imminent.
by Samuel Axon
The previous generation of the MacBook Pro.
Andrew Cunningham
The highly anticipated new MacBook Pro models with Apple-designed silicon will arrive by this November, reporter Mark Gurman said in his most recent newsletter.
Gurman, who has a strong history of accurately reporting on new Apple products from sources with direct knowledge of Apple's plans, writes that "some hiccups have led to production delays" for the new MacBook Pro computers, which analysts and consumers have been expecting any day now for most of the year.
Previous reports from the supply line suggest that the manufacturing of new Mini LED displays may be a bottleneck. Still, Gurman says that the new computers "should still go on sale by the time the current MacBook Pro hits its two-year anniversary." Context suggests he is talking about the second anniversary of the 16-inch model, not the 13-inch one. That model went on sale on November 13, 2019.
This update is expected to be a major one. Most importantly, it will move the 16-inch MacBook Pro to Apple's custom-designed silicon with a new, faster cousin to the M1 that hit the 13-inch model and other Macs late last year.
Some reports have called the new chip the M1X, and others have called it the M2. (In his newsletter, Gurman refers to it as the M1X.) In any case, it is expected to have eight high-performance CPU cores and two efficiency CPU cores. It is also expected to come in two variants, one with a 16-core GPU and another with 32 GPU cores.
For comparison, the M1 has four high-performance CPU cores and four efficiency CPU cores, and it comes in configurations with either seven or eight GPU cores.
The 13-inch MacBook Pro was updated with Apple's M1 last year, but despite the chip's strong performance, Apple treats the M1 as a low-end option, with the faster one described above destined for the 16-inch MacBook Pro—plus a new 14-inch MacBook Pro to replace the 13-inch model at the high end and possibly a new replacement for the 27-inch iMac.
Apple typically announces several products in the fall. In recent years, the company has held two events late in the year. One invariably focuses on the iPhone and Apple Watch (and this year, it may include a new AirPods refresh as well), while the other may touch on Macs or iPads. Usually, the iPhone event is held in mid-September, while the other event is later, in October or November.
14. Hospitals hamstrung by ransomware are turning away patients
The ransomware epidemic continues to grow.
by Dan Goodin
Enlarge
health.mil
Dozens of hospitals and clinics in West Virginia and Ohio are canceling surgeries and diverting ambulances following a ransomware attack that has knocked out staff access to IT systems across virtually all of their operations.
The facilities are owned by Memorial Health System, which represents 64 clinics, including hospitals Marietta Memorial, Selby General, and Sistersville General in the Marietta-Parkersburg metropolitan area in West Virginia and Ohio. Early on Sunday, the chain experienced a ransomware attack that hampered the three hospitals’ ability to operate normally.
Beginning at midnight on Sunday, the three hospitals started diverting emergency patients to Camden Clark Medical Center. The facility is an hour's drive from Sistersville General, which has 25 beds. Camden Clark is about a 25-minute drive from the other two Memorial Health System hospitals hit by the breach. Another affected facility providing critical care includes a freestanding emergency room at Belpre Medical Campus in Belpre, Ohio.
Most of the Memorial Health System facilities have also canceled all non-urgent surgeries and radiology exams for Monday and are advising patients who have an appointment with a surgeon or specialist on Monday to call ahead.
“We will continue to accept: STEMI, STROKE, and TRAUMA patients at Marietta Memorial Hospital,” officials said in a statement. “Belpre and Selby are on diversion for all patients due to radiology availability. It is in the best interest of all other patients to be taken to the nearest accepting facility. If all area hospitals are [on] diversion, patients will be transported to the emergency department closest to where the emergency occurred. This diversion will be ongoing until IT systems are restored.”
In the crosshairs
The hospitals and clinics are the latest health facilities to be hamstrung by a ransomware epidemic that has worsened over the past 36 months as it shuts down critical fuel pipelines, industrial-scale meat-packing plants, and other infrastructure that is vital to everyday life and safety. Already this year, 38 attacks on health care providers or systems have disrupted patient care at roughly 963 locations, compared with 560 sites being impacted in 80 separate incidents from all of 2020, according to Brett Callow, a threat analyst at security firm Emsisoft.
Eskenazi Health, a health care service provider that operates a 315-bed hospital, inpatient facilities, and community health centers throughout Indianapolis, Indiana, turned ambulances away last week after it was hit by a ransomware attack. Earlier this month, Sioux Falls, South Dakota-based Sanford Health also experienced a ransomware attack that caused emergency patients to be diverted to other hospitals for days while IT workers raced to restore service.
Some ransomware groups have pledged to spare hospitals, schools, and critical infrastructure from attacks, but as the recent string of attacks shows, critical health providers continue to get infected, either because of human error or because ransomware groups still consider them targets.
15. T-Mobile has been hacked yet again—but still doesn’t know what was taken
Data reportedly includes SSNs, driver license numbers, and more for 100 million people.
by Dan Goodin
T-Mobile said on Monday that hackers breached its internal servers and that company investigators are in the process of determining if the incident involves the theft of sensitive customer data.
“We have determined that unauthorized access to some T-Mobile data occurred, however we have not yet determined that there is any personal customer data involved,” the company said in a statement. “We have been working around the clock to investigate claims being made that T-Mobile data may have been illegally accessed.”
The statement came a day after Motherboard reported that a forum post was advertising a massive trove of data for sale. The post didn’t mention T-Mobile, but the seller told the publication that data related to more than 100 million people and that it came from T-Mobile servers.
The seller reportedly said that the data included Social Security numbers, phone numbers, names, physical addresses, unique IMEI numbers, and driver license numbers. Motherboard confirmed that samples of data made available by the seller “contained accurate information on T-Mobile customers.”
Learn know and Grow has been unable to confirm the authenticity of the claims made by the person who published the post and spoke to Motherboard.
By some counts, T-Mobile has experienced as many as six separate data breaches in recent years. They include a hack in 2018 that gave unauthorized access to customer names, billing ZIP codes, phone numbers, email addresses, and account numbers. In a breach from last year, hackers absconded with data including customer names and addresses, phone numbers, account numbers, rate plans and features, and billing information.
According to reporting by journalist Jeremy Kirk, the person responsible for the latest T-Mobile hack claimed that they obtained unauthorized access by exploiting a misconfigured GPRS gateway, which carriers use in 2G or 3G cellular communications.
The person who claims to have compromised T-Mobile says the company misconfigured a gateway GPRS support node that was apparently used for testing. It was exposed to the internet. That allowed the person to eventually pivot to the LAN. Proof screenshot supplied. pic.twitter.com/tBMvRBmG0r
If claims that data for 100 million people have been hacked prove to be true, this latest breach will be among the largest carrier data breaches ever.
Thanks for reading.
Contact : learnknowandgrow0@gmail.com

































Post a Comment